The Cyber Protection Console - Introduction to the Dashboard
In the Cyber Protection console, you can manage workloads and plans, change the protection settings, configure reports, or check the backup storage.
The Cyber Protection console provides access to additional services or features, such as File Sync & Share or Antivirus and Antimalware protection, Patch management, Device control, and Vulnerability assessment. The type and number of these services and features vary according to your Cyber Protection license.
To check the dashboard with the most important information about your protection, go to Monitoring > Overview.
Depending on your access permissions, you can manage the protection for one or multiple customer tenants or units in a tenant. To switch the hierarchy level, use the drop-down list in the navigation menu. Only the levels to which you have access are shown. To go to the management portal, click Manage.

The Devices section is available in simple and table view. To switch between them, click the corresponding icon in the top right corner.
The simple view shows only a few workloads.
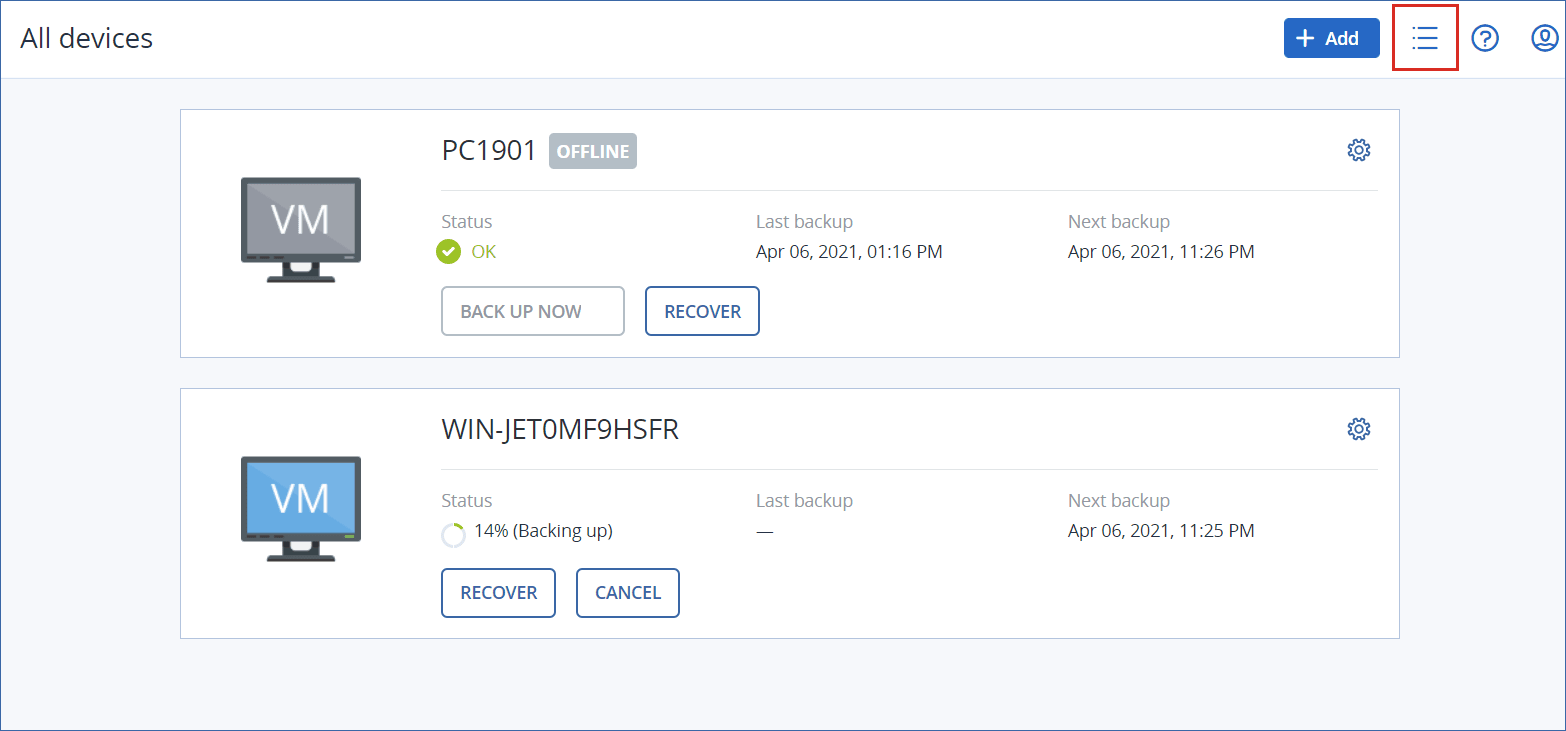
The table view is enabled automatically when the number of workloads becomes larger.
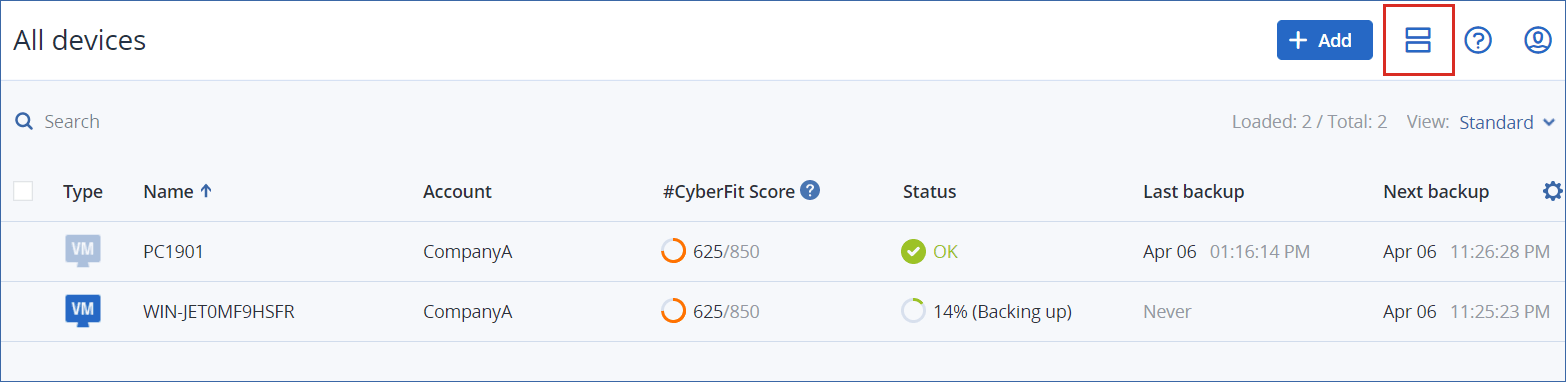
Both views provide access to the same features and operations. This document describes access to operations from the table view.
When a workload goes online or offline, it takes some time for its status to change in the Cyber Protection console. The workload status is checked every minute. If the agent installed on the corresponding machine is not transferring data, and there is no answer to five consecutive checks, the workload is shown as offline. The workload is shown as back online when it answers to a status check or starts transferring data.
To delete a workload from the Cyber Protection console
- Select the check box next to the desired workload.
- Click Delete, and then confirm your choice.
Deleting a workload from the service console does not uninstall the protection agent on the corresponding machine and does not delete the protection plans applied to this workload. The backups of the deleted workload will also be kept.
ESXi hosts and virtual machines on the following virtualization platforms can be backed up by an agent that is not installed on them—that is, in the agentless mode:
- Hyper-V
- VMware
- Virtuozzo Hybrid Infrastructure
- Scale Computing
- Red Hat Virtualization/oVirt
You cannot delete such machines individually. To delete them, you need to find and delete the machine on which the respective agent (Agent for Hyper-V, Agent for VMware, Agent for Virtuozzo Hybrid Infrastructure, Agent for Scale Computing, or Agent for oVirt) is installed.
To delete a virtual machine or ESXi host without an agent
- Under Devices, select All devices.
-
Click the gear icon in the upper right corner and enable the Agent column.

- In the Agent column, check the name of the machine where the respective agent is installed.
- Delete this machine from the service console. This will also delete all of the machines that are backed up by its agent.
For complete documentation and guide, please check this link: https://dl.managed-protection.com/u/baas/help/23.01/user/en-US/index.html#welcome-to-cyber-protection.html
If you still need any help, please feel free to Submit Ticket to our Acronis Cloud Backup Section.


 CHI
CHI EN
EN